PROTECT | CYBERSECURITY
This diagram highlights just a few uses an attacker may have for a compromised machine:
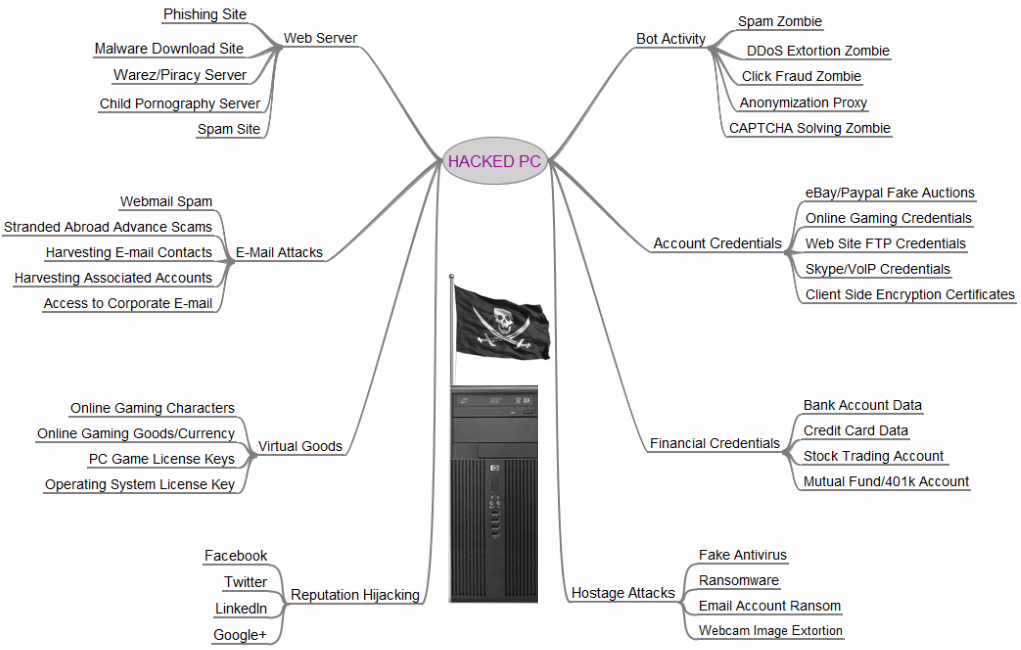
The best way of preventing such attacks is for your network to undergo thorough testing, selected and tailored to the individual needs of your company. We offer a wide variety of services and training to improve your overall security, including the following:
Vulnerability Assessments
Here we use the same tools as potential attackers to scan your business network for vulnerabilities, correcting them before they can be exploited. The vulnerabilities will be ranked in order of the risk they pose to your business, enabling us to prioritise how they are dealt with.
External Penetration Testing
An external penetration test allows us to assess the external facing network surface against the techniques and tools used by attackers and enables us to identify areas of weakness.
Internal Penetration Testing
The internal penetration test looks at the internal network from the perspective of both an authenticated and non-authenticated user. This allows the system to be critically assessed for potential exploits by rogue internal users as well as unauthorised attacks.
Phishing Assessment
The best way to counter this kind of attack is to use a tailor-made phishing simulation. This teaches staff safe habits, demonstrating key indicators in emails that they should avoid. The results of the simulation also provide a useful basis for further risk analysis and staff training.
Information Security Operations Centre (ISOC)
This is an offsite solution that will monitor your network for irregularities within data traffic that indicate an attempted compromise of your business network.
Security Training
Staff training is absolutely crucial. A new report from Kapersky Lab has revealed that 90 per cent of breaches are caused by human error. Our training can cover areas such as the safe use of company hardware in public places and identifying potential malicious software and emails. We can provide this training in a professional manner that will increase staff confidence and help prevent breaches.












